Recently I had to set up load balancing for Microsoft Active Directory Federation Services (ADFS) 3.0 environment. There is not a whole lot of information out there on load balancing of ADFS 3.0. Most of the guides and documentation that are out there today are based on ADFS 2.0
The diagram below illustrates a typical ADFS deployment scenario utilizing hardware load balancers such as Netscaler or F5 appliances.
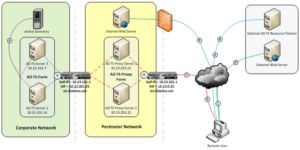
Why you need to do this.
Server Name Indication (SNI) is a feature of SSL TLS and both Web Application Proxy and AD FS 2012 R2 use it to enable simpler deployment and remove networking prerequisites. Some client applications don’t support SNI but there is an easy way to workaround this using a fallback certificate. In this blog we will explain what SNI is, how it works and what to do if you have non-SNI capable clients.
In this case the client (i.e. the Netscaler) does not support SNI for back end services. hence the requirements below. The proxy servers will only reply if the host header is present and will not respond directly via IP address. One of the main issues with the load balancing of the latest ADFS is that it doesn’t bind the certificate or service to the IP address.
ADFS Server & Proxy Server Configuration
On each of the ADFS servers and Web Application Proxy Servers for the ADFS services you will need to do the following.
- Open PowerShell
- Run the following command in the PowerShell Window
- netsh http show sslcert
- Review the output of the command and notate the following field

- Certificate Hash
- Application ID – Copy including brackets
- Run the following command in the PowerShell Window
- netsh http add sslcert ipport=<IPAddress:port> certhash=<certhash> appid=<appid> certstorename=MY
- Fields
- IPAddress:port such as 0.0.0.0:443 for example
- note 0.0.0.0 will bind to all IP addresses on server. Can use specific IP
- certhash – copied from netsh http show sslcert
- appid – copied from netsh http show sslcert
- IPAddress:port such as 0.0.0.0:443 for example
- Note: On several of the systems that I ran the powershell command on I had to put single quotes around the appid before and after the brackets Without the bracket the error was “The Parameter is incorrect”
- Example of this would be below
- netsh http add sslcert ipport=<IPAddress:port> certhash=<certhash> appid='<appid>’ certstorename=MY
- Example of this would be below
- Fields
- netsh http add sslcert ipport=<IPAddress:port> certhash=<certhash> appid=<appid> certstorename=MY
Netscaler Configuration.
You will need to create attach the monitor to either the services or service groups for ADFS 3.0 Servers & Proxy Servers. In my case all services & service groups were configured for SSL Bridge
ADFS Monitor Configuration
add lb monitor mon-https-ADFS3 HTTP-ECV -send “GET /federationmetadata/2007-06/federationmetadata.xml” -recv “adfs3.website.com/adfs/services/trust” -LRTM ENABLED -secure YES
ADFS Proxy Monitor Configuration – Note the addition of the custom header. This is required for the proxy server configuration
add lb monitor mon-https-ADFS3-PROXY HTTP-ECV -customHeaders “host: adfs3.website.comrn” -send “GET /federationmetadata/2007-06/federationmetadata.xml” -recv “adfs3.website.com/adfs/services/trust” -LRTM ENABLED -secure YES
Replace website adfs3.website.com with your particular company website.
You can find more information below at the following links
- How to support non-SNI capable Clients with Web Application Proxy and AD FS 2012 R2
- Hardware Load Balancer Health Checks and Web Application Proxy AD FS 2012 R2
- https://www.netscalerrocks.com/netscaler/load-balance-adfs-3-0-using-netscaler/
ADFS is used in a variety of services and I hope you found this helpful. Now signing off.

